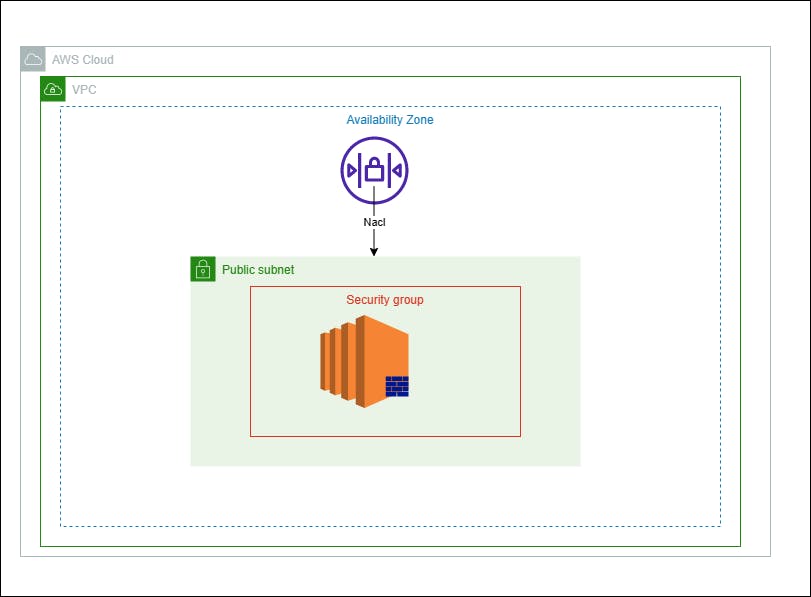
Network Access Control Lists (NACLs) and security groups are both used to control inbound and outbound traffic to a Virtual Private Cloud (VPC) in AWS. However, they serve different purposes and are applied at different levels in the network.
Network ACLs are applied at the subnet level and control traffic for all instances in a specific subnet. They are similar to a firewall at the network level and can be used to deny or allow traffic based on IP address, port, and protocol. The default network ACL is configured to allow all traffic to flow in and out of the subnets with which it is associated.
Security groups, on the other hand, are applied at the instance level and control traffic for an instance. They can be used to allow or deny traffic based on IP address, ports, and protocol. Security groups also have a default deny-all rule attached to an instance.
An Operating System (OS) firewall, such as iptables on Linux, can also be used to control traffic to a specific instance. OS firewalls are applied at the instance level, similar to security groups, and can be used to allow or deny traffic based on IP address, ports, and protocol.
To understand how these different security measures work together in a VPC, consider the following example. A user wants to set up a web server in a VPC and needs to allow incoming traffic on port 80. The user will set up an instance in a subnet, this subnet by default allows all traffic through the Network ACL.
Therefore, the user would launch an instance of the web server in the subnet and apply a security group to the instance that also allows incoming traffic on ports 80 and 22. Finally, the user would be able to access the instance through the port that has been allowed by the security group, then the OS firewall on the instance can be configured to allow incoming traffic on port 80. In this example, all three security measures (NACL, security group, and OS firewall) are working together to allow incoming traffic on port 80 to the web server.
NACLs, security groups and OS firewalls are all used to control inbound and outbound traffic to a VPC in AWS. They are applied at different levels in the network, NACLs at the subnet level, Security groups at the instance level and OS firewalls at the operating system level. Together, they provide a multi-layered security approach to protect the instances in your VPC.
In summary, NACLs are the most superior option for controlling traffic for multiple instances, security groups are the most superior option for controlling traffic for a single instance, and iptables is a powerful option but it requires knowledge of Linux command-line interface and can be complex to set up and manage. All three options provide an approach to protect the instances in your VPC.